Get 40 Hours Free Developer Trial
Test Our Developers for 40 Hours at No Cost - Start Your Free Trial →
Role-based access control, or RBAC, is one of the most used access control methods in organizations today. Organizations rely on RBAC to simplify permission management when handling security for countless users, as it feels too complicated. It provides a clear and efficient solution.
This article explains how RBAC works and provides real-world examples. It also highlights the main benefits that. On top of that, it shares strategies to implement RBAC in different settings, such as cloud platforms like AWS & Azure. You will also find useful tips to set up a strong access management system.
What is Role-Based Access Control?
Role-based access control connects permissions to roles tied to job duties instead of focusing on individual people. It works by placing users with similar tasks into specific roles, forming a layer between the users and the permissions they can access.
Definition and purpose of RBAC access control
RBAC uses a system to handle IT privileges by connecting roles to permissions, then assigning users to these roles. It avoids giving permissions to users. Instead, it ties them to set roles that match their job titles, departments, or duties within an organization. The main goal is to make managing user access simpler and to cut down on administrative tasks.
RBAC focuses on establishing a clear structure that matches access permissions with business roles. It ensures that users have access to the tools or data needed for their assigned tasks, following the principle of least privilege. As a result, companies can improve security measures and make managing access easier.
How RBAC differs from Discretionary and Mandatory access control
Unlike Discretionary access control (DAC), resource owners decide who gets access; RBAC gives centralized control over permissions through set roles. On the other hand, mandatory access control (MAC) uses strict security labels and clearance levels, where RBAC allows more flexibility by letting you define roles to fit specific needs.
Each system meets unique security needs. MAC ensures confidentiality, while DAC prioritizes availability. RBAC, on the other hand, emphasizes integrity. RBAC can work alongside other access control methods or function on its own, showing how flexible it is in different security setups.
Role-based access control example in enterprise settings
Imagine a hospital using RBAC. Administrators set up specific roles such as “Nurse” and “Doctor,” each with defined permissions. Nurses can check medications and add information to electronic health records, but are not allowed to prescribe drugs. Doctors, however, can prescribe medication and perform other medical tasks.
In business environments, customer service teams may look at billing details but do not deal with payments, while billing professionals manage payments but avoid changing service information. This split helps keep responsibilities divided across the company.
Read Also: How Microservices Architecture Helps Modern Software Development?
How Role-Based Access Control Works
Setting up role-based access control depends on three key connected parts that make up its working foundation. Knowing these parts helps organizations create strong policies to manage access.
User-role-permission mapping explained
RBAC relies on linking users, roles, and permissions in a structured way. It does not connect users to permissions directly. Instead, it uses roles as links that hold permissions together. Organizations assign users to roles according to their jobs and skills. With this setup, roles carry permissions, and users access what they need by joining those roles. This method makes things easier to handle because roles may shift more often than the permissions tied to them.
Role hierarchies and inheritance models
Role hierarchies form organized connections among roles mirroring an organization’s chain of command. In these structures, higher-ranking roles are shown at the top, and lower-ranking roles are placed below them. The inheritance system lets permissions pass upward. This means that roles at a higher level gain all the permissions that the roles below them have. For example, in healthcare, a primary care physician’s role includes permissions in both the physician role and the healthcare provider role.
Hierarchies generally follow three models:
- Tree structure: Bottom-up permission flow
- Inverted tree: Top-down inheritance
- Lattice: Combined approach allowing bidirectional inheritance
Separation of duties and least privilege enforcement
Dividing responsibilities, also called separation of duties (SoD), is a key security approach used in RBAC to stop conflicts of interest. This approach is divided into two main types:
- Static Division of Duties (SSD): Stops users from having roles that cannot be held together at the same time.
- Dynamic Division of Duties (DSD): Lets users take on conflicting roles but blocks their use in the same session.
The principle of least privilege makes sure users get the permissions they need to do their tasks. These measures work together to lower security risks by keeping access to sensitive data limited.
RBAC in Cloud and Automation Environments
Cloud services increase the demand to manage access. RBAC plays a key role in managing infrastructure today.
AWS role-based access control with IAM roles
IAM roles in AWS work as specific identities with permissions, but they do not rely on regular long-term credentials such as passwords or access keys. These roles are not the same as standard user accounts. They are meant to be taken on by those who need them, offering temporary security credentials during role sessions. This method works well in cases like granting access between accounts, using mobile apps, or giving access to external auditors.
RBAC in Kubernetes and container orchestration
Kubernetes RBAC controls which users can perform which actions and in which areas. It uses four key components: Roles, ClusterRoles, RoleBindings, and ClusterRoleBindings. Roles grant permission within a single namespace, whereas ClusterRoles apply across multiple namespaces. These elements link roles to API endpoints by working with API servers. This setup strengthens security by giving users the access they need, reducing risks if credentials are stolen.
Automating role assignments with policy engines
Automation gets rid of the hassle of managing RBAC manually. Tools such as Open Policy Agent allow organizations to handle policies going further than simple RBAC features. By integrating GitLab, Keycloak, and OIDC, teams can set up automated role assignments, build scalable group structures, and match access controls to their company’s framework. At the same time, tools like Jinja2 can be used to create RBAC policies from user details.
Advantages of Role-Based Access Control
Businesses that use role-based access control see real advantages in many areas of their operations.
Improved operational efficiency through centralized role management
RBAC simplifies managing access by linking permissions to specific roles instead of individual users. It can lower administrative workload by as much as 65% and cut down access-related help desk issues by around 25 to 40%. Onboarding speeds up by 30%, which helps new employees start working right away. Offboarding is also safer because access gets revoked when roles are deleted.
Enhanced compliance and audit readiness
RBAC provides clear and reliable audit records to show adherence to regulations. Companies say they cut compliance costs by 30 to 45 percent and shorten audit prep time by about 60 percent. This clarity helps meet rules under HIPAA, SOX, GDPR, and similar regulatory systems.
Reduced risk of data breaches
RBAC reduces the risk of unauthorized access by using least privilege rules. A key point is that 62% of data breaches occur due to the misuse of privileged credentials, which RBAC works to prevent. It limits possible breaches by restricting how far attackers can move if credentials are stolen. In our last blog, on data cleaning and transformation, we explained how to reduce data breaches.
Scalability for growing teams and systems
RBAC grows with organizations as they scale. Role-based provisioning can cut down manual work by as much as 70% helping organizations handle access management no matter their size.
Best Practices for RBAC Implementation
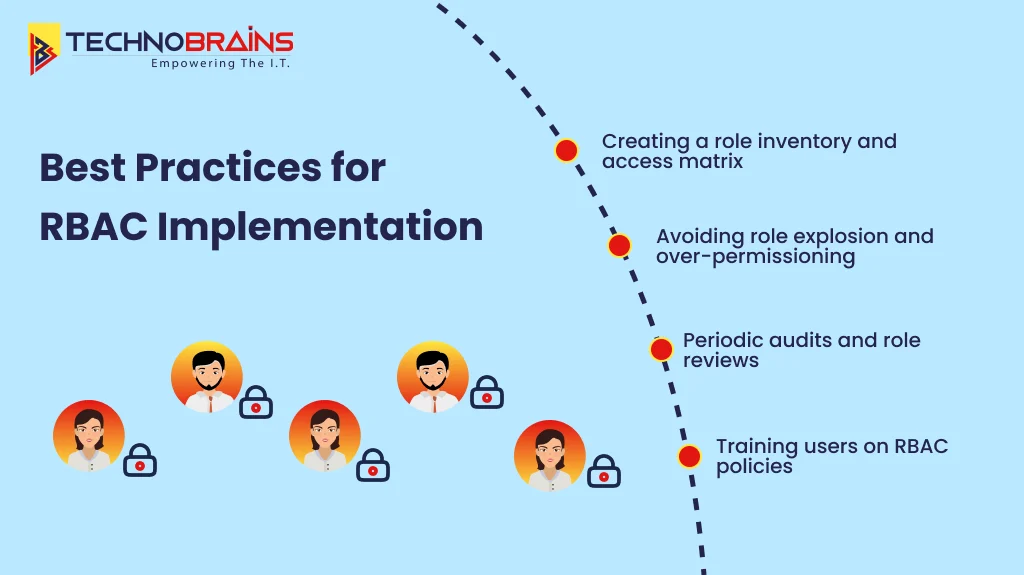
To implement role-based access control, take a structured approach that meets security requirements while staying user-friendly.
Creating a role inventory and access matrix
First, identify what access your organization needs. Make a detailed list of roles within the organization, keeping the focus on job duties instead of individual people. Write an RBAC policy that explains the rules, purpose, and goals. Then, use a role-permission chart to match permissions to roles. Use this chart to see and confirm how access is assigned.
Avoiding role explosion and over-permissioning
Organizations create too many specialized roles, sometimes causing extra administrative work. To stop this from happening, you should group permissions into clear and reusable roles. Build a role system that matches how your organization is set up. Start by giving users the minimum permissions they need. Also, get rid of roles that overlap or do the same thing to avoid redundancy.
Periodic audits and role reviews
Frequent audits play a key role in keeping RBAC effective. Companies need to review role assignments every few months or each year. They should take away permissions when employees leave or switch jobs. Doing this helps find outdated roles, unneeded access, and possible security risks.
Training users on RBAC policies
Obtain support from executives to make cybersecurity training a priority. Create training tailored to specific roles, so employees see how it applies to their work. Keep reinforcing these lessons as new threats appear.
Conclusion
Role-Based Access Control plays a key role in managing access in today’s security systems. It gives organizations an organized way to protect their digital resources. In this article, we discussed how RBAC makes managing permissions easier by linking access rights to job roles instead of assigning them to each user. This method lowers the effort needed for administration and boosts security in businesses, no matter their size.
As cyber threats become more advanced and rules from regulators get stricter, organizations will need role-based access control to stay secure and efficient. RBAC’s clear framework allows businesses to set proper access limits while adapting and growing. In the end, it gives today’s companies what they need most – easier management and stronger security for their critical digital resources.
Looking to simplify access management? Contact TechnoBrains to get professional guidance or implementation of RBAC.