Get 40 Hours Free Developer Trial
Test Our Developers for 40 Hours at No Cost - Start Your Free Trial →
When it comes to enterprise stack security, software applications are the weakest link. In The State of Application Security, 2020, Forrester says the majority of external attacks occur either by exploiting a software vulnerability (42%) or through a web application (35%).
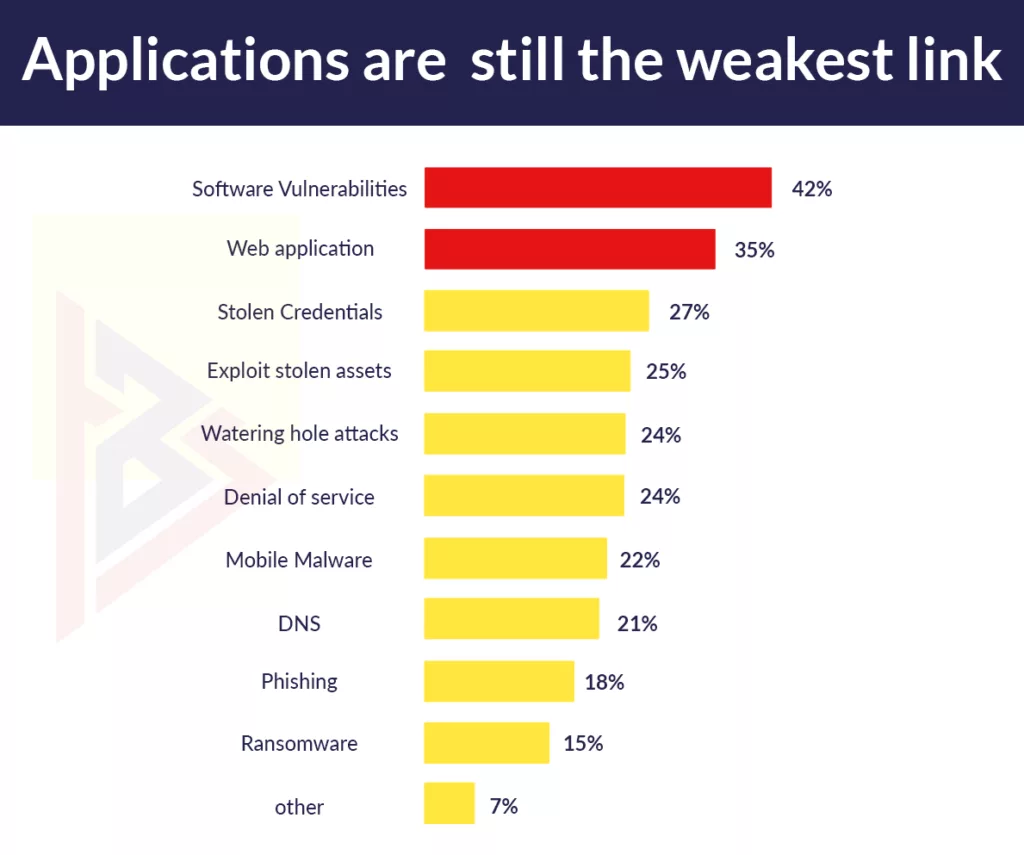
based on Forrester’s The State Of Application Security 2020
Developers are under pressure to release features as soon as possible as applications become more complex and development timelines shrink. To achieve differentiated and compelling application functionality, developers increasingly rely on third-party libraries. This shift towards open-source components makes security practices more complex for companies. New frameworks such as containers and APIs further complicate application security.
With developers being pressured to release new features constantly. Organizations face a very real risk of security failing to keep pace. Security can be achieved by incorporating application security best practices into the software development life cycle and implementing them.
Read here about the approximate cost of the development of a mobile app.
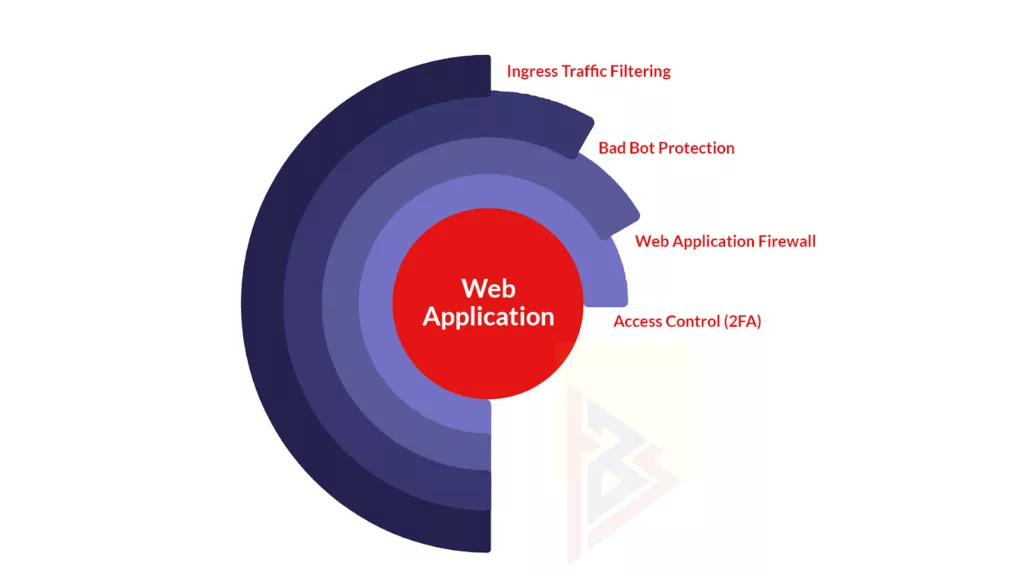
Why is web security testing important?
Dont include Imperva
Testing Web applications and their configurations for security vulnerabilities is the goal of Web security testing. Application layer attacks (i.e., targeting HTTP-based applications) are the primary targets. It is common to submit different types of input to a Web application to provoke errors and cause it to behave unexpectedly. In these so-called “negative tests”, the system is inspected for behavior that is not intended.
It is also important to note that Web security testing is not simply about testing the security features. These are implemented in the application (e.g., authentication and authorization). It is also necessary to test that other features (e.g., business logic and input and output validation) are implemented in a secure way. Secure access to the Web application functions is the goal.
Types of Web App Security Tests: Overview & Importance
- Dynamic Application Security Test (DAST)- For compliance with regulatory security assessments, this automated application security test is ideal for internally facing, low-risk applications. A combination of manual web security testing and DAST. It is the best approach for medium-risk applications and critical applications that are undergoing minor changes.
- Static Application Security Test (SAST) – This approach to application security tests both manually and automatically. An application can be tested in this way without having to run it in a production environment. Furthermore, it allows developers to systematically detect and eliminate software security vulnerabilities by scanning source code.
- Penetration Test- Especially for applications undergoing major changes, this manual application security test is ideal. Assessments include business logic and adversary-based testing to identify advanced attack scenarios.
- Runtime Application Self-Protection (RASP)- A number of technological techniques are used in this evolving approach to application security to instrument an application in such a way that attacks can be monitored as they execute and, ideally, blocked in real-time.
Read here, why your next app should be developed in Flutter.
How does application security testing reduce your organization’s risk?

Majority of Web Application Attacks
- The SQL injection technique
- Cross-Site Scripting (XSS)
- Execution of commands remotely
- Path Traversal
Attack Results
- Content that is restricted
- Accounts that have been compromised
- Malicious software installation
- Revenue lost
- Customers lose trust
- Reputational damage
- As well as much more
Today’s Web environment is prone to a wide range of problems. In addition to knowing how an application can be exploited, knowing the potential outcomes of the attack will help your company preemptively address the vulnerabilities and accurately test for them.
Mitigating controls can be applied during the early stages of the SDLC after identifying the root cause of the vulnerabilities. In addition, a Web application security test can take advantage of the knowledge of how these attacks work to target known points of interest.
To manage your firm’s risk, you must understand the impact of an attack, since it can be used to gauge the vulnerability’s total severity. As a result of a security test, determining the severity of detected issues can help you prioritize remediation efforts efficiently and effectively. Minimize your firm’s risk by starting with issues of critical severity and moving on to issues of lower impact.
A potential impact assessment of each application in your firm’s application library prior to identifying an issue can assist with prioritizing application security testing. When web security testing has an established list of high-profile applications, we can schedule the testing to target your firm’s critical applications first so that the risk against your business can be lowered.
So, do you want to know the difference between React Native and Ionic, click here to read our blog.
What features should be reviewed during a web application security test?

Several features should be examined during the security testing of Web applications, but the list is not exhaustive. Your organization could be exposed to serious risk by an inappropriate implementation of each.
- Application and server configuration. Defects may be related to encryption configuration, Web server configurations, etc.
- Input validation and error handling. The most common injection vulnerabilities, including SQL injection and cross-site scripting (XSS), are the result of poor input and output handling.
- Authentication and session management. Vulnerabilities that could lead to impersonation of users. A strong credential policy is also essential.
- Authorization. Verifying the application’s ability to prevent vertical and horizontal privilege escalation.
- Business logic. This type of logic is essential to most business applications.
- Client-side logic. This type of feature is becoming more common in modern, JavaScript-heavy websites, as well as websites using other client-side technologies (e.g., Silverlight, Flash, Java applets).
Following are the Top 10 Web Application Security Practices your Organization Should Already Be Implementing:-
#1 Track Your Assets
If you don’t know what you have, you can’t protect it.
For which functions or apps do you use specific servers? In which web apps do you use open-source components?
Do you think it’s not important to track your assets? It is very important to remember which software is running within each application – just ask Equifax, which was fined $700 million for failing to protect the data of over 145 million customers. One of the credit rating agency’s customer web portals was compromised after an open-source component, Apache Struts, was not patched. The company says it wasn’t aware the customer portal used the vulnerable open-source component.
The sooner you start tracking your assets, the fewer headaches and disasters you’ll have later. As organizations scale their development, this process can feel like a Sisyphean task.
You should also classify your assets, noting those that are critical to your business’s functions and those that are of lesser importance. Then, you can assess threats and remediate them later.
#2 Perform a Threat Assessment
If you make a list of what you need to protect, you can then identify the threats you face and how they can be mitigated.
How would hackers be able to break into your application? What existing security measures do you have in place? What additional tools are required?
You must answer these and other questions as part of your threat assessment.
Yet, you must also be realistic about the level of security you can enjoy. No matter how secure you make your system, you can still hack it. Furthermore, you need to be honest about the measures your team can maintain over time. You can risk having your security standards and practices ignored by pushing for too much. Take security seriously and don’t rush it.
Use the following formula to evaluate your risk:
Risk = Probability of Attack x Impact of Attack.
Risk can also be thought of as the probability of something happening versus the severity of the consequences. Even though it would be catastrophic if a whale did fall out of the sky and crush you, it is unlikely that it will happen. A mosquito bite on a hike, on the other hand, is quite likely, but not likely to cause significant harm beyond a few itchy bumps.
#3 Stay on Top of Your Patching
Installing the latest patches on your operating systems? Are you using third-party software? The chances are you’re lagging behind, meaning you’re exposed.

One of the most important steps you should take to ensure the security of your software is to update the software, either from a commercial vendor or from an open-source community. When a vulnerability is discovered and responsibly reported to the product or project owners, it is published on security advisory sites and databases such as the WhiteSource Vulnerability Database. If possible, a fix should be created and released prior to publication, providing users with an opportunity to secure their software.
However, if you do not apply a patch when one becomes available, you will not benefit from improved security.
If you are worried that updating to the latest version can break your product, automated tools can help a lot. Any day of the week, you should prioritize updating and patching as part of your application security best practices.
#4 Manage Your Containers
In recent years, containers have grown in popularity as more organizations adopt the technology due to its flexibility, which simplifies the process of developing, testing, and deploying components across various environments throughout the software development lifecycle (SDLC).
It is generally accepted that containers offer security advantages that give them an advantage. In addition, because of their self-contained OS environment, they are segmented by design, thereby lowering the level of risk. Yet, containers continue to be vulnerable to exploits such as a breakout attack, in which the isolation has been broken. Containers may also contain a vulnerability in the code stored within them.
For CI/CD pipeline security, you should scan for vulnerabilities from start to finish, including in your registries.
In addition to these scans, best practices for application security in working with containers also include important tasks such as signing your own images with tools such as Docker Content Trust if you are using Docker Hub, or Shared Access Signature if your team is using Microsoft Azure.
#5 Prioritize Your Remediation Ops
There have been an increasing number of vulnerabilities in recent years, and this trend shows no signs of slowing down anytime soon. Consequently, developers are busy with remediation. For teams hoping to keep their applications secure while remaining sane, prioritization is essential.
Threat assessments are performed based on the severity of a vulnerability (CVSS rating), the criticality of the impacted application, and a number of other factors. You need to know whether the open-source vulnerability actually impacts your proprietary code when it comes to open-source vulnerabilities. Ineffective and not a high risk even if the CVSS rating of the vulnerable component is critical if it does not receive calls from your product.
Smart strategies are ones that prioritize the most pressing threats first, based on the factors present, and leave the low-risk ones for later.
#6 Encrypt, Encrypt, Encrypt
The OWASP Top 10 has included encryption of data at rest and in transit for years, making it a requirement for any application security best practices list.
Man-in-the-middle attacks and other forms of intrusion can expose sensitive data when you fail to lock down your traffic properly. When you store passwords and user IDs in plain text, for instance, you put your customers at risk.
Make sure you use SSL with an updated certificate as part of your basic checklist for encryption. Don’t let yourself be left behind now that HTTPS is the standard. Hashing is also recommended.
Additionally, you should never “roll your own crypto” as they say. Consider security products that are supported by a dedicated team with the experience to do the job right.
#7 Manage Privileges
You don’t have to give access to everything to everyone in your organization. Applications and data are only accessible by those who need them. Following network security best practices and application security best practices.

There are two reasons for this. The first thing you need to do is prevent a hacker from using marketing credentials to gain access to a system. It contains other more sensitive data, such as finance or legal. Insider threats are also a concern, be it unintentional – such as losing a laptop or sending the wrong attachment to an email – or malicious. The Principle of Least Privilege of providing employees with only the data they need when it comes to accessing data could reduce your exposure compared to having no controls in place.
#8 Embrace Automation for Your Vulnerability Management
The security of their applications has become increasingly important to developers in the past few years, especially when it comes to tasks like vulnerability management. To address security’s leftward shift, developer teams are testing early and often, pushing as many of their security checks early in the development process when it is easier and cheaper to fix vulnerabilities. For managing the unwieldy testing process due to the sheer quantity of vulnerabilities, developers require automated tools.
To find potential security vulnerabilities in your proprietary code, static application security testing (SAST) and dynamic application security testing (DAST) can be employed during development. Security holes are closed with SASTs and DASTs, however, proprietary code makes up a relatively small portion of your overall code.
In more than 92% of all modern applications, open-source components make up 60-80% of your codebase. Your application security checklist should prioritize securing open-source components.
Using software composition analysis tools, teams can run automated security checks and reports throughout the SDLC. Identifying each open source component in their environment and indicating which of them has a known vulnerability that poses a security risk to your applications.
You can better manage your vulnerabilities by shifting your automated testing for open-source security issues to the left.
#9 Penetration Testing
A top application security best practices list would be incomplete without mentioning pen testing. Even though automated tools help catch the vast majority of security issues. Testing with pen and paper allows you to poke and prod your app to find weaknesses. If a determined hacker tries to break into your application, good pen testers know exactly what steps they need to take.
Hacking firms can be hired or freelancers can participate in bug bounty programs like BugCrowd and HackerOne. Your company should sponsor a bug bounty if you don’t already.
If you hire pen testers, it is far better to pay for them than to deal with the consequences of a real breach.
#10 Be Careful with Tokens
In spite of the fact that this is an easy one to secure, many developers do not properly secure their tokens for third parties.

By searching popular developer websites, you can easily find unsecured tokens online. Instead of storing token details elsewhere, developers simply include them in their open-source repositories.
The basic application security best practice is to properly secure your third-party tokens. You shouldn’t leave tokens you’ve purchased lying around in your code for anyone to take.
Web Application Security as Basic Practices
Each of the best practices outlined here should be integrated into your organization’s continuous development process. Your company’s applications and data are at risk if you don’t minimize the risk. Follow these steps to minimize the risk.
Avoiding the mistakes that others are likely to make is one way to stay ahead of hackers, so you’re harder to target for attacks. There will never be a perimeter or application security measure that is fully hack-proof.
However, following these basic best practices can go a long way towards keeping your application not worth the trouble for the hackers. We at TechnoBrains make sure all the applications we develop are free from security threats. We have experienced web developers who make sure to handle all the security threats.